Objective Security Management
We provide expert knowledge and tailored technical solutions, including managed services, to comprehensively address your cybersecurity and compliance needs. Navigating the evolving landscape of cybersecurity threats and regulations, we ensure your day-to-day operations run smoothly while maintaining robust digital defenses.
Services
Solutions
We maintain and operate your IT Security. From outsourced firewall operation to security management. Our experts have long experience in deploying and operating IT security solutions.
Oliver Van Assche
Cyber Security Solutions
Advisory & Assurance
From penetration test to management system implementation, we support you in identifying threats and establishing information security measures to protect your valuable assets.
Sebastian Strobl
Advisory and Assurance Services
Compliance
Want to enter a new market or know what requirements your IT will need to fulfil to comply to GDPR or PCI DSS? Our experienced professionals will help you overcome these hurdles for your business.
Martin Stöfler
Compliance Management Services
Safeguarding your digital assets is our paramount priority. With a proven track record of success, we specialize in assessing and fortifying both infrastructure and applications against evolving cyber threats. Our team brings extensive and enduring experience across diverse markets and industries, ensuring that our clients receive tailored solutions that address their unique security challenges. In an era where digital risks are continually on the rise, we stand as your trusted partner, committed to delivering cutting-edge cyber security services that fortify your defenses and empower you to navigate the digital landscape with confidence.
Latest News

1 Year Until DORA: A Compact Overview for Financial Service Providers
As we stand at the threshold of January 2024, the clock is ticking for financial service providers across Europe. The Digital Operational Resilience Act (DORA) is set to come into full effect in January 2025, marking a significant shift in the regulatory landscape. This impending regulation underscores the critical importance of digital resilience in an era where cyber threats loom large and operational continuity is paramount. In this blog, we’ll delve into the essence of DORA, outline the key requirements it imposes on financial entities, and provide a strategic roadmap to ensure compliance within the one-year timeframe.

Cloud Security
IT services in the cloud are becoming more and more popular these days. Many companies have already made their way to the cloud or are in the process of migrating their infrastructure to the cloud. Obviously, this offers a number of advantages: fast service delivery, high scalability, seemingly unlimited resources, and very high availability at a reasonable price. In addition, you do not have to purchase your own server hardware and do not have to maintain it. Despite all these advantages, the security of the company’s applications and data in the cloud should not be overlooked. Even if conventional security technologies cannot be integrated into the cloud solution so easily, the security objectives remain the same: preventing unauthorized access, preventing data loss and maintaining availability.
So, what needs to be considered when it comes to cloud security?
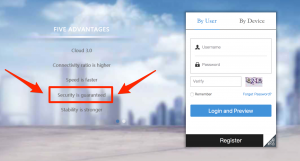
IP Camera Security Horror
Would you like to buy a nice (and cheap) wireless surveillance camera to monitor your entrance or other areas of your property? That was exactly what I wanted and after doing some research I found hundreds of offers for wireless cameras with Wi-Fi, SD-Card Storage, Pan & Tilt functionality and much more between 20 and 60 Euros. These are sold through various websites and shops, most of them look quite similar and also offer more or less the same functionality. I randomly picked a model with the features I required and ordered it online. About 3 weeks later the package arrived, but while waiting for it I rethought the whole idea of buying security equipment from an unknown manufacturer called “e-scam” and planned for a small review before really putting it to use.
Our Products
What Our Clients Say